Home > News & Blog > How to implement Security
How to Implement Embedded Security into Your Microcontrollers
The Critical Role of Embedded Security in IoT Devices

Missed the previous editions of our Simply Security Series? Catch up here:Who, What, When, Where, and Why.
At EPS Global, we’ve partnered with leading edge security companies, such as IAR Systems, to build a robust, secure infrastructure for embedded security implementation. With the systems that are in place, our provisioning platform for embedded security is a trusted, secure environment with thousands of hours of engineering experience and know-how invested in it. When you come to talk to EPS Global about your embedded systems security needs, we’ll work with you to understand the threats to your business and how to design a process that secures your product throughout its lifecycle.
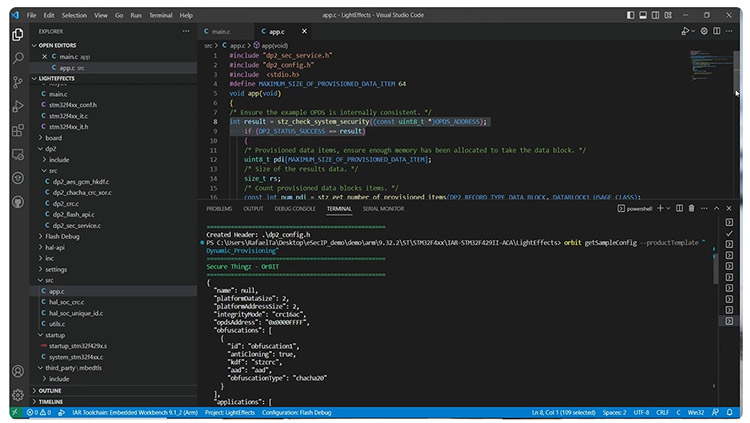
Screenshot of IAR's ESecIP Utility. Download Now
Firstly lets look at the issue of trusting a third party with your embedded security needs. The reason why we can be trusted, is that we provide our customers with the tools needed for them to secure themselves. At no point in the cycle of securely provisioning your chips, does any third party, including EPS Global, have access to your firmware, software, keys or certificates, unless its been encrypted with industrial grade encryption techniques. Any data that leaves your premises will be fully encrypted and the only thing that can decrypt it is an industrial grade, FIPS complaint high security module.

The Hardware Security Module, also known as a "HSM", is a pivotal piece of equipment in the embedded security process. These modules are as the name illustrates, highly secure. It is impossible for anybody to tamper with them, having tamper-proof mechanisms protecting the unit's enclosure as well as software. If any HSM unit is opened, or tampered with, all data within it is erased immediately.
The HSM is capable of supporting many different elements of the embedded security process. Authenticating an identity, creating an on-boarding certificate or as I’m going to talk about in more detail below, encrypting firmware and software.
How Embedded Firmware and Software can be Encrypted
To show how embedded firmware and software can be encrypted, here’s the first two stages that are required utilizing an encryption utility from IAR systems called ESecIP and a HSM.
At your customer premises, firmware and software is developed. Using EsecIP, your firmware and software is encrypted using the security credentials of a HSM in an EPS Global programming centre. From that point of encryption, the only thing that can decrypt the encrypted package is the HSM, which of course is fully tamper-proof.
The encrypted package is then sent to EPS Global. This can be sent by any medium as it's now completely secure in its encrypted state. Only when the encrypted package is loaded into the HSM, will it be decrypted. As this is a FIPS compliant HSM, it’s impossible to read out or modify anything inside the HSM. It is now fully secure.
So what happens next now that your firmware and software is loaded securely into the HSM inside EPS Global’s programming centre?
Automated Secure Provisioning
The next stage of the process involves the highly automated programming machines of EPS Global. The HSM effectively becomes directly connected to the microcontroller that will be sitting in a socket of the programming machine. This is where the EPS programming machine, that was typically used for flash programming, ultimately becomes a provisioning machine with the added functionality of the HSM.
The HSM now prepares a uniquely encrypted file that will be provisioned into the microcontroller. This means that even if the interface between the HSM and programmer machine was attacked, only encrypted data would be seen and hence would be useless.
The unique encrypted file is then programmed into the microcontroller. This now means that your firmware and software has been transferred from your premises, to EPS Global and finally into your microcontroller, in a completely encrypted state and has made every microcontroller to appear to have unique firmware and software image.
To a hacker, or somebody trying to steal your IP, this is a nightmare scenario as they have to break through leading edge encryption to get any visibility of the original firmware or software. Without this encryption, it's really quite straightforward for hackers to interfere with the firmware and do something malicious or to clone the device making cheaper, inferior versions of your product which may even cause harm to the end user resulting in brand reputational damage.
Embedded Security Provisioning Workflow
Here’s a diagram that illustrates the tools which are required. All of this is provided as part of a complete solution when working with EPS Global on embedded security.
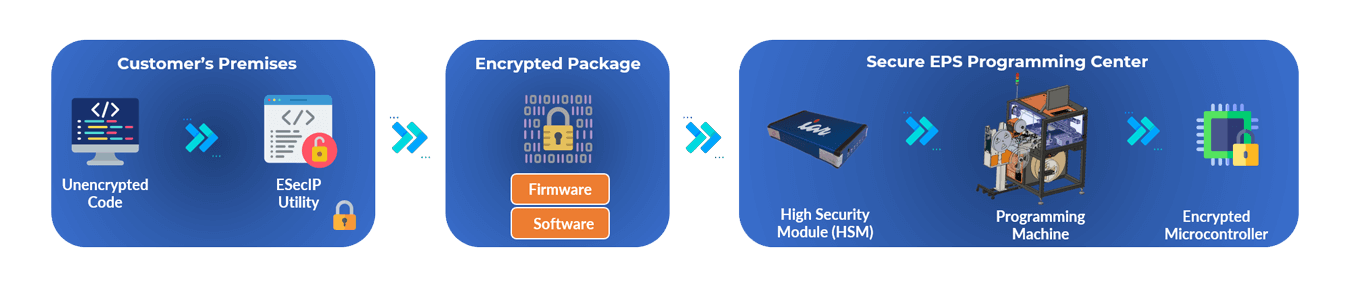
There are further aspects of this process which much be considered carefully, such as how will the microcontroller decrypt its now unique firmware and software? This capability is enabled through the EsecIP tool. Without going into detail, there are thousands of hours of engineering time that has been invested into tools such as EsecIP, enabling very complex procedures to be taken care of very simply. This is the advantage of utilizing and engaging with a solution provider such as EPS Global and IAR systems for embedded security.
As mentioned earlier, this system can be adopted for a range of embedded security functions, all of which have the same complexity, but made very simple by the tools.
- Generating an authenticated identity
- Creating and provisioning unique cloud on-boarding certificates
- Creating and injecting customer keys and certificates.
All of these processes can be integrated into one swift provisioning operation, making this a very scalable and efficient way to implement provisioning for embedded security.
We're Here to Help
The key to navigating the complexities of embedded security lies in understanding the multifaceted nature of the challenges, embracing collaborative approaches, and choosing comprehensive, expert-driven solutions like those offered by EPS Global Component Services, trusted by Tier 1 OEMs and Contract Manufacturers all over the world.
By prioritizing code quality, recognizing the hidden costs of DIY (do-it-yourself) solutions, overcoming internal resistance, and adopting a holistic security framework that covers all stages of a product’s lifecycle, organizations can build robust, secure, and future-proof embedded systems.
At EPS Global, we understand the complexities and challenges of implementing robust embedded security. Work with us to ensure your products are secure, compliant, and ready to face the evolving landscape of cyber threats.
Don't wait for a security breach to take action. Secure your embedded systems today with EPS Global's expert solutions. Contact us now to learn how we can help you strengthen your connected products and protect your business.









