Home > News & Blog > When is the right time for Embedded Security?
When is the right time for Embedded Security?
The Critical Role of Embedded Security in IoT Devices

The question of "When is the right time for embedded security?" has never been more critical. As we continue our Simply Security Series (read Who, What, Where, and Why here), we’ve mentioned that the production of smart products and sensitive IP are increasing at a rate never seen before in the electronics industry. Gaining unlawful access to products and their owner's confidential information has become a trade in its own right, making it super important for every product manufacturer to take responsibility for securing their product.
According to a 2023 ThreatLabz report, there was 400% growth in IoT-targeted cyber attacks over 2022. Manufacturing has been the sector most targeted for IoT attacks, with 54.4% of reported attacks.
We’ll discuss the topic of “When is the right time for embedded security?” in two parts. Part 1 will be about how legislation is forming which is dictating cut off points for making products secure. Part 2 will be about when to start thinking about security in your product's life cycle and what options are available at different stages of development.
Part 1 - Legislation
To address the growing threat of cyber-attacks against the rising number of IoT devices, country and regional governments are enacting legislation and programs aimed at stricter security. Earlier this year, the UK became the first country to mandate IoT cybersecurity standards, and the EU requires products sold in the EU to meet a set standard. Additionally, the US is making big steps forward advancing on IoT regulation with federal laws being enhanced and particular states enacting their own legislation. The US has now implemented an optional labelling program which identifies when a wireless product meets the security criteria advised by NIST. As consumers become more aware of this, and the risks involved with unsecure wireless communication, it’s likely the approved products will become more widely used than non-approved.
Here's a quick overview of the main legislation you need to be aware of if you intend to sell your connected device into the UK or EU markets.
UK Product Security and Telecommunications Infrastructure (PSTI) Act
 This landmark legislation, which came into effect on 29th April 2024 mandates that manufacturers of consumer IoT products adhere to specific security requirements. These include using unique passwords, fully reporting security issues or vulnerabilities, and providing regular security updates.
This landmark legislation, which came into effect on 29th April 2024 mandates that manufacturers of consumer IoT products adhere to specific security requirements. These include using unique passwords, fully reporting security issues or vulnerabilities, and providing regular security updates.
Let’s consider the unique password requirement for a moment. On the face of it, this can seem quite trivial, of course we should all have unique passwords. However, consider it from a manufacturing perspective. With manufacturing, anything “unique” usually costs money. That’s because it breaks the normal manufacturing flow. The same could be considered with implementing unique passwords. Putting what is effectively a unique ID into a product at its “birth” stage can be very challenging and possibly expensive. Especially when considering how many people have access to the product and systems during the manufacturing process. How easy could it be to add a “rogue” identity into the system?
The answer to the implementation of unique passwords is using systems such as EPS Global’s embedded security provisioning services which adds this functionality to standard programming operations. Powered by security appliances from IAR Systems, EPS Global are able to provision a randomly generated password into any memory or microcontroller at the very beginning of the manufacturing process, guaranteeing that nobody has the capability to access or modify it. As this is an automated process and can be integrated with the firmware programming, costs to add this feature are relatively minimal.
EU Cyber Resilience Act

The initial requirements to this legislation are as follows:
- Security by Design: Manufacturers will be required to incorporate security features into their products from the earliest stages of development.
- Vulnerability Disclosure: Manufacturers will need to have a process in place for disclosing and addressing vulnerabilities in their products.
- Security Updates: Manufacturers will be obliged to provide regular security updates to their products for a specified period of time.
- Documentation: Manufacturers will need to provide clear documentation on the security features of their products and how to use them securely.
Security by design is a fundamental principle within the EU Cybersecurity Act, requiring that cybersecurity considerations be integrated into the design, development, and lifecycle of connected products. This means that security is not an afterthought, but a core aspect of the product's development from the outset.
A proactive approach to embedded security is essential, instead of reacting to security vulnerabilities after a product is released. Security by design ensures that potential risks are identified and addressed during the planning and development stages. One of the highest threats in a product's lifecycle is during the manufacturing process. Because so many people get access to a product during this stage that could maliciously manipulate the product, it becomes an essential stage to secure. This doesn’t mean that manufacturing has to be done in-house, but it does mean that any code that leaves the trusted company must be secure.
The Act mandates that a manufacturer:
- Implements a secure software development process
- Practices secure design and vulnerability remediation
- Practices responsible vulnerability reporting disclosure
- Uses multifactor authentication (if applicable)
- Is free from hard coded secrets
- Uses strong cryptography
- Ensures user data is identified and secured
The implementation of embedded security techniques is a fundamental part of this legislation. If a wireless product hasn’t got an authenticated identity and hasn’t got secure firmware, there is very little chance that it will gain certified status which will negatively impact its ability to be sold in the EU.
Part 2 – When to Implement Embedded Security in a Product's Lifecycle
There are multiple stages of an embedded product where security can be considered. It’s important to consider that its never too late to implement security. During the early stages of development, it’s true that it is easier to select an architecture and tools with security in mind, but as technology has advanced, adding security at the later stages of development can now also make a huge impact.

During the early stages of development, it’s possible to select design tools that have security at their core. An example of this is IAR’s Embedded Trust. Embedded Trust enables a whole suite of security functionality which can be designed into your product from the very outset.
As an example of where Embedded Trust can win over at the beginning of a project is the way that it can create a complete security context which defines the security environment of the product. Within this context, the definition of the secure boot configuration, the device's memory allocation and application update process is all configured within an easy to understand and easy to implement environment.
No longer do firmware engineers need to be security experts to implement embedded security, there are tools such as ESecIP which make it very easy. This security context is then realised during the manufacturing process with dedicated security appliances which implement the unique encryption per device and installs the relevant keys and certificates needed for decryption and authentication.
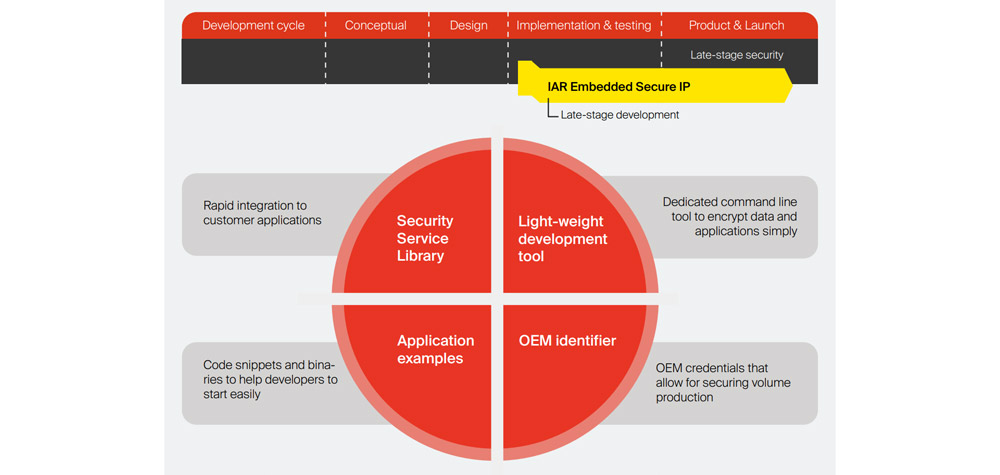
ESecIP Utility - Enabling Embedded Security during late-stage development.
If we now consider the later stages of development, where perhaps the firmware has already been written but security was initially not required or considered. There are still some very effective tools which can help to secure the product.
As talked about earlier, the manufacturing stage is an extremely vulnerable part of a product's life. Potentially lots of companies involved, giving access to products that could easily be modified by malicious actors. With the tools and systems now available, it's very simple to add a layer of encryption to the firmware which makes it impossible to be modified. Depending on the threat level or risk, this could be encryption throughout the manufacturing stage, or it could even be encryption to the chip, which means it is protected when it leaves manufacturing. Yes, all this can be done after the firmware has been completed.
For the latter solution, encryption to the chip, firmware files need to be added, but existing code doesn’t need to be modified. To enable this, IAR have a product called Embedded Security Intellectual Property, or ESecIP which enables this later stage security and is fully compatible with EPS Global provisioning services.
The message is clear: there has never been a more important time to prioritize the security of your embedded products. Whether you're in the early stages of development or working with an existing product, solutions exist to enhance your security posture.
EPS Global's embedded security provisioning services offer flexible solutions that can be integrated at various stages of your product lifecycle, ensuring you stay ahead of both cyber threats and regulatory requirements. Don't wait for a security breach to act.
Early or Late, Implement Embedded Security Now!
Contact EPS Global today to learn how we can help secure your connected devices and protect your business in an increasingly connected world. You can get started on your journey towards robust embedded security for free here:
Legislation is now enforcing that companies must take this seriously and if breaches occur and it can be proven that basic security principles were not taken, a company can be held liable. In terms of the lifecycle of a product, security can be considered and implemented at any stage using tools designed to make security simple.
We're Here to Help
The key to navigating the complexities of embedded security lies in understanding the multifaceted nature of the challenges, embracing collaborative approaches, and choosing comprehensive, expert-driven solutions like those offered by EPS Global Component Services, trusted by Tier 1 OEMs and Contract Manufacturers all over the world.
By prioritizing code quality, recognizing the hidden costs of DIY (do-it-yourself) solutions, overcoming internal resistance, and adopting a holistic security framework that covers all stages of a product’s lifecycle, organizations can build robust, secure, and future-proof embedded systems.
At EPS Global, we understand the complexities and challenges of implementing robust embedded security. Work with us to ensure your products are secure, compliant, and ready to face the evolving landscape of cyber threats.
Don't wait for a security breach to take action. Secure your embedded systems today with EPS Global's expert solutions. Contact us now to learn how we can help you strengthen your connected products and protect your business.









