Home > News & Blog > Identity – Digital Certificates & Signatures
Identity – Digital Certificates & Signatures
Part IV Secure Provisioning: Essential Security Measures for the IOT

Incase you missed Part I - What is Secure Provisioning?, Part II - Encryption: Symmetric and Asymmetric Keys, or Part III - Building a Hardware Root of Trust, you can catch up here.
Identity
Public Key Infrastructure is a standards-based security technology that has been used to secure network connected devices for some years now. It covers many use cases and provides secure encrypted communications and mutual authentication between devices, services and users. Through the use of digital certificates every connected 'thing' can be bound, by the use of public keys, to entities such as people and organizations. The use of these certificates creates a chain of trust between the connected device and a certificate authority that issued the certificates. However, in a similar way that the RoT is the basis of the security of a microcontroller system, a unique identity is the key to a valid PKI.
So, what's the big deal about identity? Can I simply use the Unique ID, or even the UUID (Universally Unique ID) that is readable from most microcontrollers available today? No, this is not an identity, it's only an identifier. For PKI to work we need a randomly generated cryptographic key pair to be generated for every single device manufactured. The key pair must be provisioned into the RoT of the microcontroller. The private key must be protected by the hardware RoT and the public part is held in a certificate, both of which are provisioned during manufacturing. The certificate will be signed by a certificate authority thus providing a means of authentication for the identity. This is what identity is, not just a number but a cryptographic technique whereby a 'thing' is identified by a randomly generated key pair. The public part of the key pair is provided in the form of a certificate which has been signed (authenticated) by a trusted certificate authority. The private part of the key pair is used to prove the identity.
Digital Signatures
A digital signature is a mechanism used for verifying the authenticity of digital messages or documents. A valid digital signature provides the receiver with strong confidence that the message or document was created by a known sender (authentication) and that the message was not altered in transit (integrity). Let us examine the process of creating a digital signature and how it relates to our problem of securing our software.
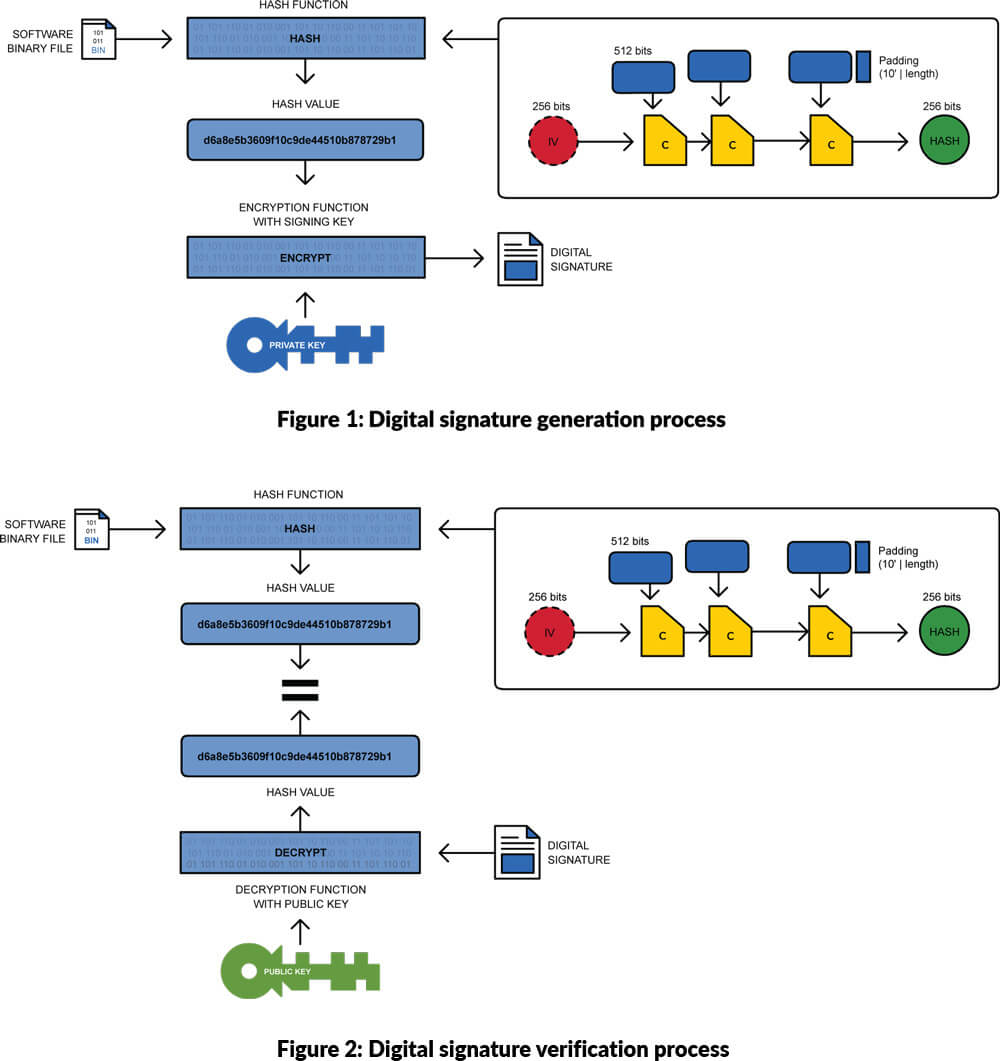
We want to send a software image to a recipient, and we want to use a digital signature to provide the receiver with confidence that the software comes from the sender (authentication) and was not tampered with during transmission (integrity). Figure 1 shows the process flow.
Firstly, we take our software image, a binary file, and we process it using a HASH function. A HASH function takes an arbitrary data block (our binary file) and maps it to a bit string of fixed size. For example, if we were to process our binary file using a SHA-256 HASH function the output would be a unique 256-bit value. If we were to change one bit of the binary file and repeat the process, it would result in a completely different 256-bit value. This mechanism is used to check the integrity of a data block.
To create a digital signature, we now encrypt the output of the HASH function (the 256-bit value) using the private asymmetric key of the sender. It is important to highlight that the private key MUST be held securely by the sender. This is the basis of PKI. The receiver now receives both the binary file and the digital signature associated with it. Using the sender's public key, the receiver decrypts the signature thus exposing the HASH value. The receiver processes the binary file using the same HASH function. If the resulting HASH value is the same as the one decrypted from the digital signature, the binary file's integrity is intact (see Figure 2).
A digital signature is a mechanism used for verifying the authenticity of digital messages or documents.
We’ll be moving onto the Hardware Security Module next, why it is trusted and how to package a binary file for the HSM.
In the meantime, if you have any questions or require secure provisioning services get in touch, we have local engineering and sales teams ready to help. You can find a full list of our locations here.
Alternatively if you have any questions or would like us to focus on additional topics around IOT security and provisioning in future blogs, don’t hesitate to let us know: programming@epsglobal.com.
Til next time…









