Home > News & Blog > Encryption: Symmetric and Asymmetric Keys
Encryption: Symmetric and Asymmetric Keys
Part II of the Secure Provisioning: Essential Security Measures for the IOT series

Incase you missed Part I: What is Secure Provisioning?, you can catch up here.
This is a complex subject but is probably the key element in ensuring your software is protected and not visible to unauthorized persons. Encryption is often the first thing that comes to mind when the subject of security is raised.
There are two public key cryptographic techniques that are popular today. These are Rivest, Shamir, & Adleman (RSA) and Elliptic Curve Cryptography (ECC). There is a great deal of information available when comparing the two techniques. However, from the embedded engineer's viewpoint, it is necessary to understand what microcontroller resources are needed to implement these techniques. ECC seems to be the clear winner here with the main advantages being:
- Very fast key generation Fast signatures
- Smaller key sizes for equivalent RSA security levels
- Good standards support
- Good key exchange mechanism
Basically, for ECC, it comes down to fast and small (short computational bursts and small flash memory needed for key storage and transmission. As an example, a 256-bit ECC public key has approximately the same level of security as a 3074-bit RSA public key.
Ideally, any secure provisioning service should support the latest cryptographic technologies so as to maintain compatibility with choices made by development engineers in their security architectures. There is often a requirement for the secure provisioning service to generate keys at the programming head in order to support the need to inject keys into bare-metal microcontrollers. More of this later (see Identity). If the cryptographic techniques used in the security of the software in the product are compatible with the technology available in the secure provisioning system, it all adds up to less complexity and better security during manufacturing.
 Symmetric and Asymmetric Keys
Symmetric and Asymmetric Keys
We have mentioned the use of cryptographic keys, but it is necessary to examine these in a little more detail. There are two types of cryptographic keys that are used for encryption/decryption, these are keys. Symmetric keys are used to encrypt/decrypt large amounts of data, for example software images (Figure 1). A weakness of symmetric keys is that the key that is used to encrypt the data, e.g. software image, is the same key needed to decrypt the data. This means the key must be shared between sender and receiver.
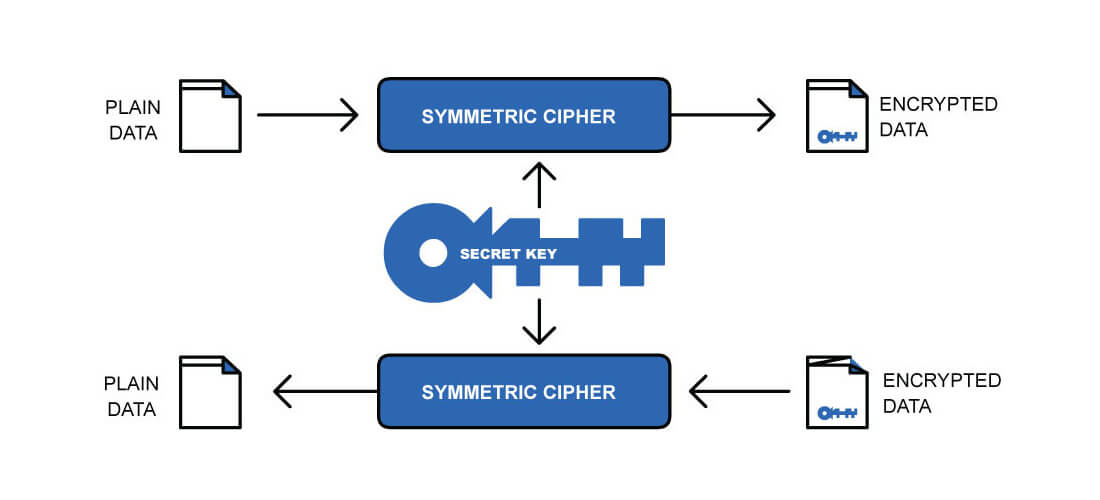
1. Symmetric Key Usage
Asymmetric keys come in pairs, a public and private key. They are used as part of the PKI to authenticate data by the use of digital signatures. For asymmetric keys, any one of the keys (public or private) can be used to encrypt the data (much smaller amounts of data) but can only be decrypted by the other key (Figure 2a & 2b).
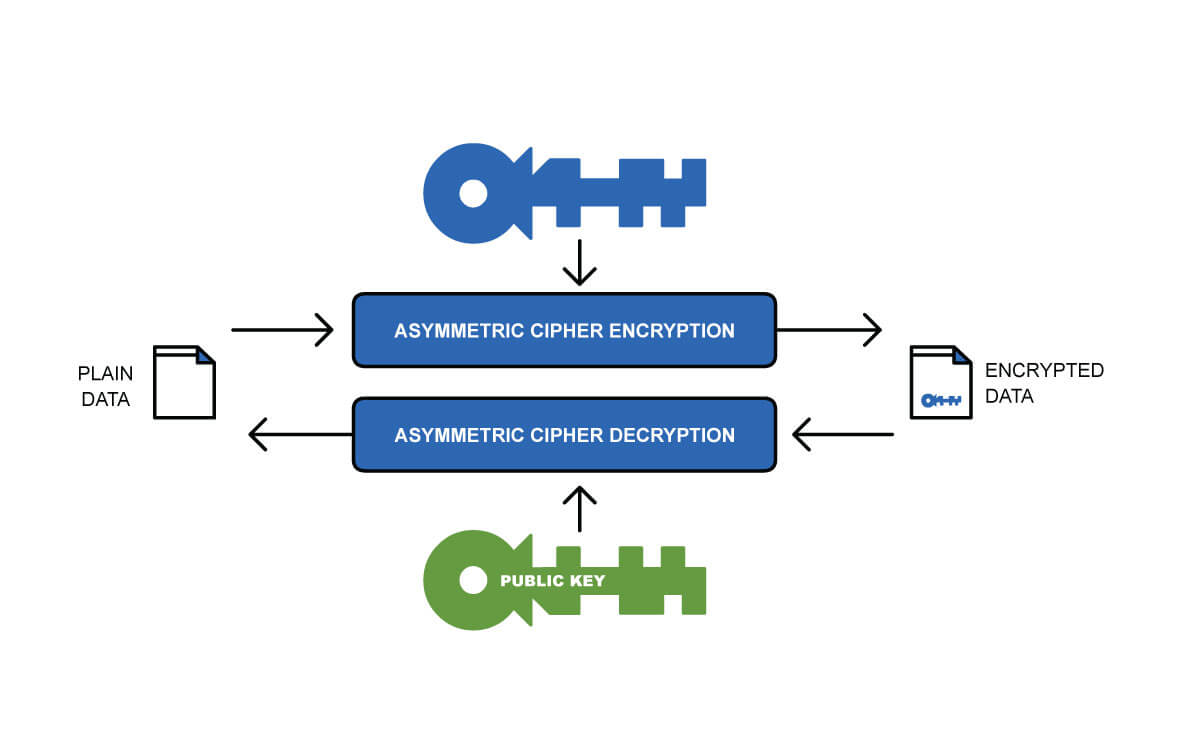
2a. Asymmetric Key Usage
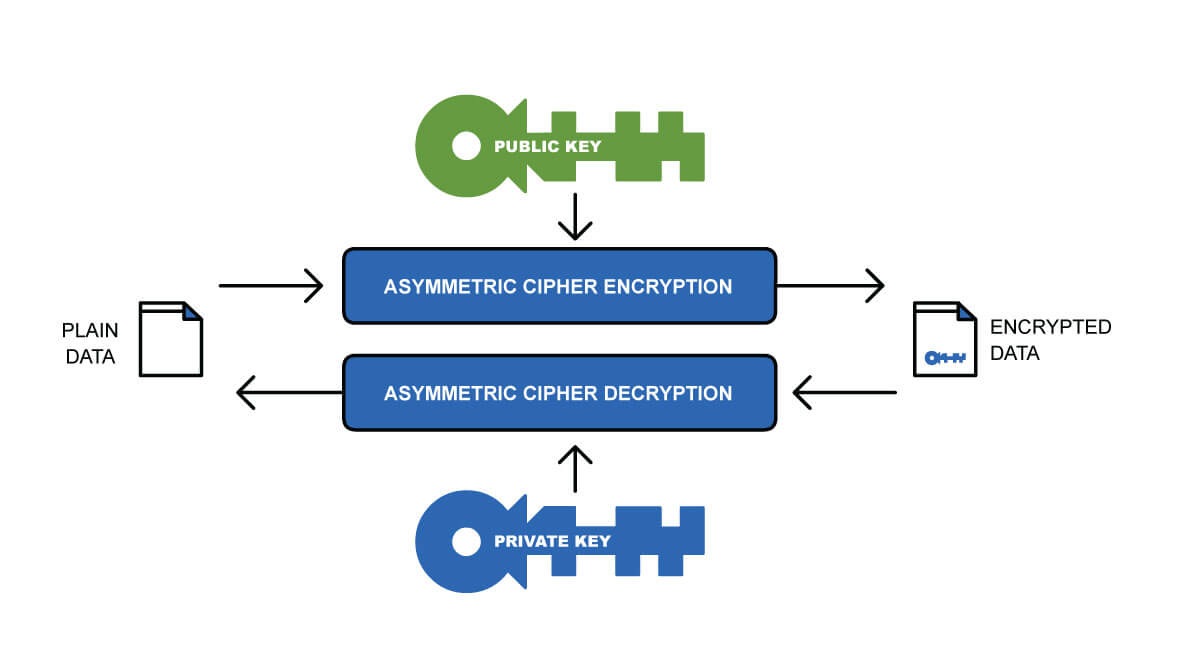
2b. Asymmetric Key Usage
Coming up in Part III, you can discover how secure provisioning ensures that the RoT is programmed into the bare-metal microcontroller in a secure manner.
In the meantime, if you have any questions or require secure provisioning services get in touch, we have local engineering and sales teams ready to help. You can find a full list of our locations here.Alternatively if you have any questions or would like us to focus on additional topics around IOT security and provisioning in future blogs, don’t hesitate to let us know: programming@epsglobal.com.
Continue Reading: Part III - Building a Hardware Root of Trust.









